Certification
Certification: the basis of trust
How can you gain from your valuable data? – by sharing it with others in trustworthy partnerships. These partnerships are based on data spaces. It is therefore our goal to establish data spaces that guarantee a safe collaboration between partners.

Entrusting data to IDS
The foundation of IDS is trust, which is established through a rigorous, transparent certification process. The most important component of a data space is the IDS Connector. To make sure that each IDS Connector behaves as it should, it is certified against specific security standards and so is any participant in data sharing. On this basis of trust the participants can start their actual exchange of data.
Since 2022, IDSA has been operating the IDS Certification Scheme aimed at certifying the interoperability, compatibility, and trustworthiness of data space connectors.
With the completion of standardization of the Dataspace Protocol, the IDS Certification Scheme will evolve to assess interoperability modules based on automated testing.
By enabling adopters to choose from a series of certified data space connectors, we will ensure that their efforts are focused only where they are needed: on identifying the best use cases for data sharing that support their objectives and entrepreneurship.
Transparency through clear processes
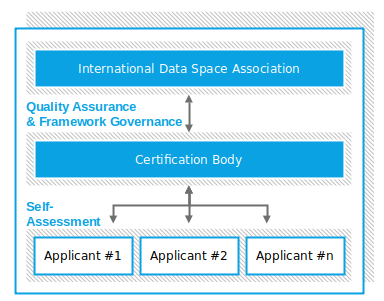
For the certification of participants and components, we are using a certification scheme which defines the rules, and standards of the certification process. The IDS certification scheme follows best practices from internationally accredited certification concepts.
Core component certification
Here we evaluate and certify the core components of IDS. Do they provide the required functionality and security?
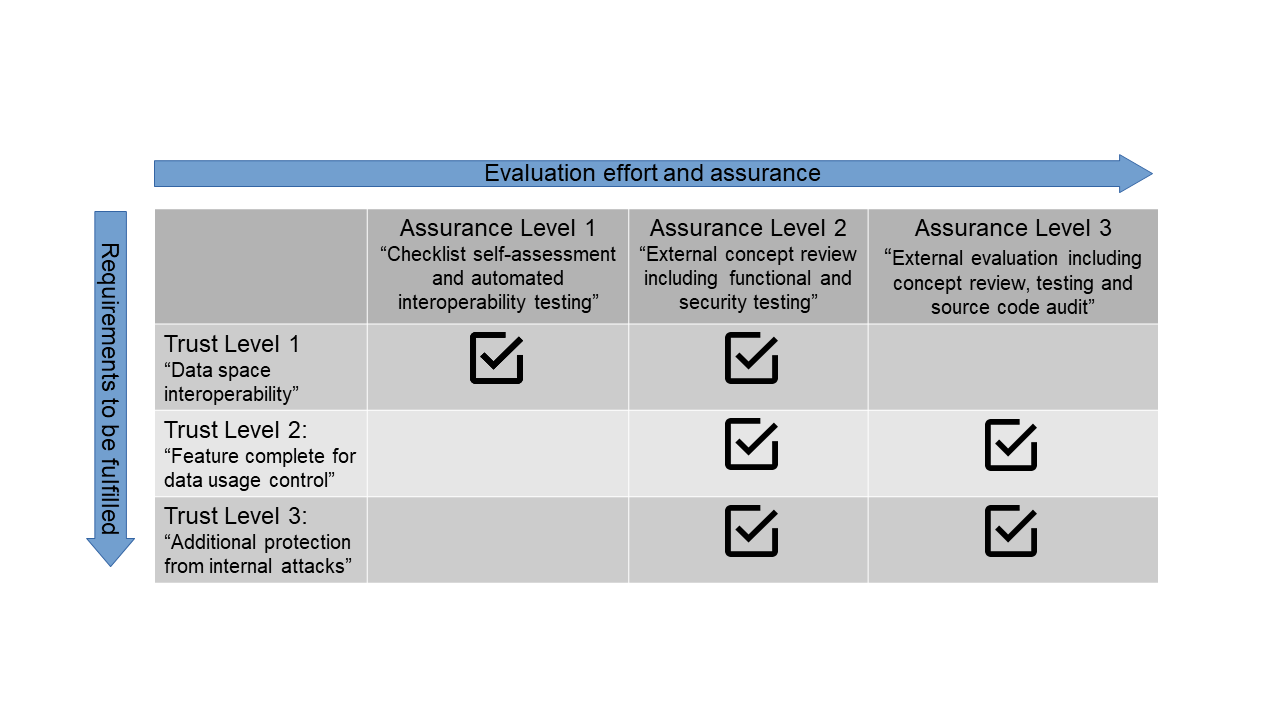
There are two assurance levels available
Different companies and organizations have different data sharing needs, timelines, and budgets. For that reason, we offer two types of assessments to allow for more flexibility. Have a look at the first and simpler one below to the left and see a more complex variant below to the right.
The assurance level 1 checklist approach covers basic requirements for taking part in IDS. It allows you to prove that your IDS Connector is not only interoperable with any other connector in a data space but also complies with the IDS Reference Architecture Model. It is prepared by yourself and focuses on basic implementation but also on efficient, non-bureaucratic processes.
-
- Before starting the assessment, your component needs to go through the IDS reference testbed
- The assessment is based on a questionnaire, which can be accessed via the IDS Certification portal
- You’ll receive your certificate after you’ve filled in the questionnaire, uploaded the testing log files to the portal and have been assessed based on that information
The checklist approach certification generates significant value for companies; it is the beginning of a journey towards trustworthy and interoperable data spaces to grow your business.

All IDS components must meet a list of certification criteria to prove the provision of the required functionality, interoperability, and level of security.
The IDS assurance level 2 concept review certification is a wonderful way to show your partners in data sharing that you are committed to giving them the highest level of trust. It is proof that your IDS component complies with all requirements in terms of functionality and security. The concept review certification is performed by an independent third party: the IDS evaluation facilities. All IDS evaluation facilities must go through an extensive approval process for added security.
The external concept review includes the examination of documentation as well as the practical testing of the Connector, to ensure the correct implementation of the functional and security requirements. IDS Assurance Level 2 strikes the right balance between an independent review and the corresponding costs. This level can be combined with all three trust levels.
Receiving the third-party IDS certificate demonstrates:
-
- comprehensive reviews and testing
- independent validation
- credibility by data sharing partners

All IDS components must meet a list of certification criteria to prove the provision of the required functionality, interoperability, and level of security.
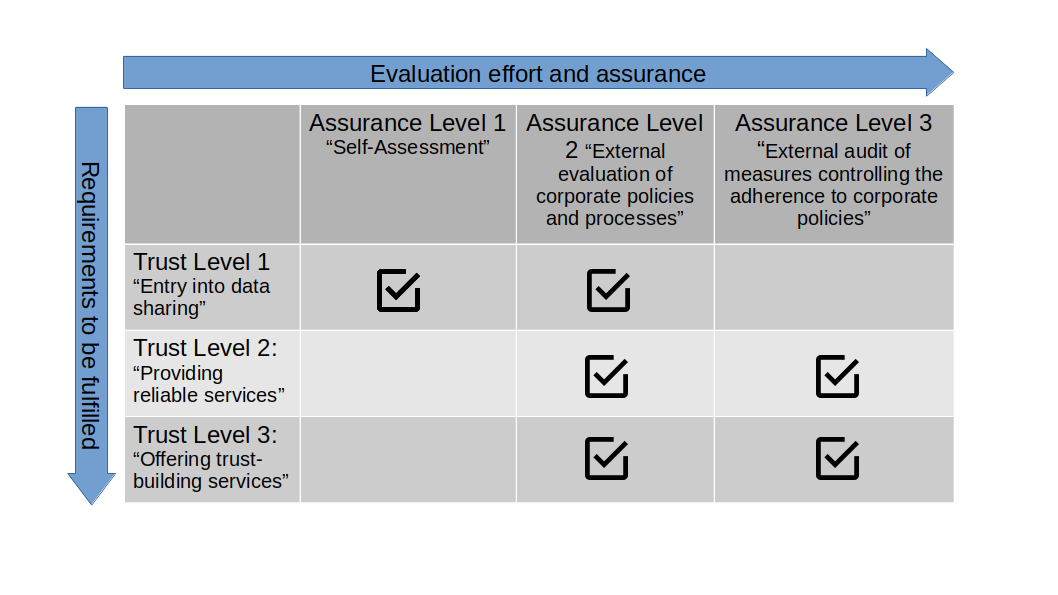
Operational environment certification
This evaluation provides an assessment of the trustworthiness of the physical environment, processes, and organizational rules.
The self-assessment covers basic requirements for taking part in IDS. This allows smaller companies to clear the first hurdle to IDS Certification and try out data spaces participation. It is prepared by yourself and focuses on basic but also on efficient, non-bureaucratic processes
-
- The assessment itself is based on a questionnaire, which can be accessed via the IDS Certification portal.
- You’ll receive your certificate after you’ve filled in the questionnaire and have been assessed based on that information
The IDS Self-assessment Certification generates significant value for companies; it is the beginning of a journey towards trustworthy and interoperable data spaces to grow your business.

All IDS components must meet a list of certification criteria to prove the provision of the required functionality, interoperability, and level of security.
IDS evaluation facilities
IDSA implementations should be reliable and robust. To this end, data sharing between certified entities using certified core components is encouraged. IDS evaluation facilities are accredited laboratories for validating IDS components according to standards formulated by IDSA.
The evaluation facilities independently oversee the validation of commercial IDS components developed by companies in various industries. They are also responsible for preparing the corresponding evaluation report, which is sent to IDSA for subsequent certification.
SQS Software Quality Service

SQS is the first approved IDS Evaluation Facility and the accredited laboratory for validating components according to the IDSA standards for rusted and sovereign data sharing.
CFIEC China Future Internet Engineering Center

Recognized as an IDS Evaluation Facility, CFIEC advances international collaboration and supports IDS-based data space technologies and architectures.
Low barriers to certification
IDS Certification is compatible with commonly used security standards like ISO 27001 and IEC 62443. This way, you can reuse existing documentation and setups for IDS certification – and minimize your effort significantly.
Certified data connectors
Which data connectors are certified? What are the evaluation results? Are there any application remarks? Discover a list of all certified data connectors. Click on the button for more details.
T-Systems Data Intelligence Hub (DIH) connector

VTT DSIL connector

TNO TSG Connector

Engineering TRUE Connector

GATE Dataspace Connector

Huawei Exchange Data Space Connector

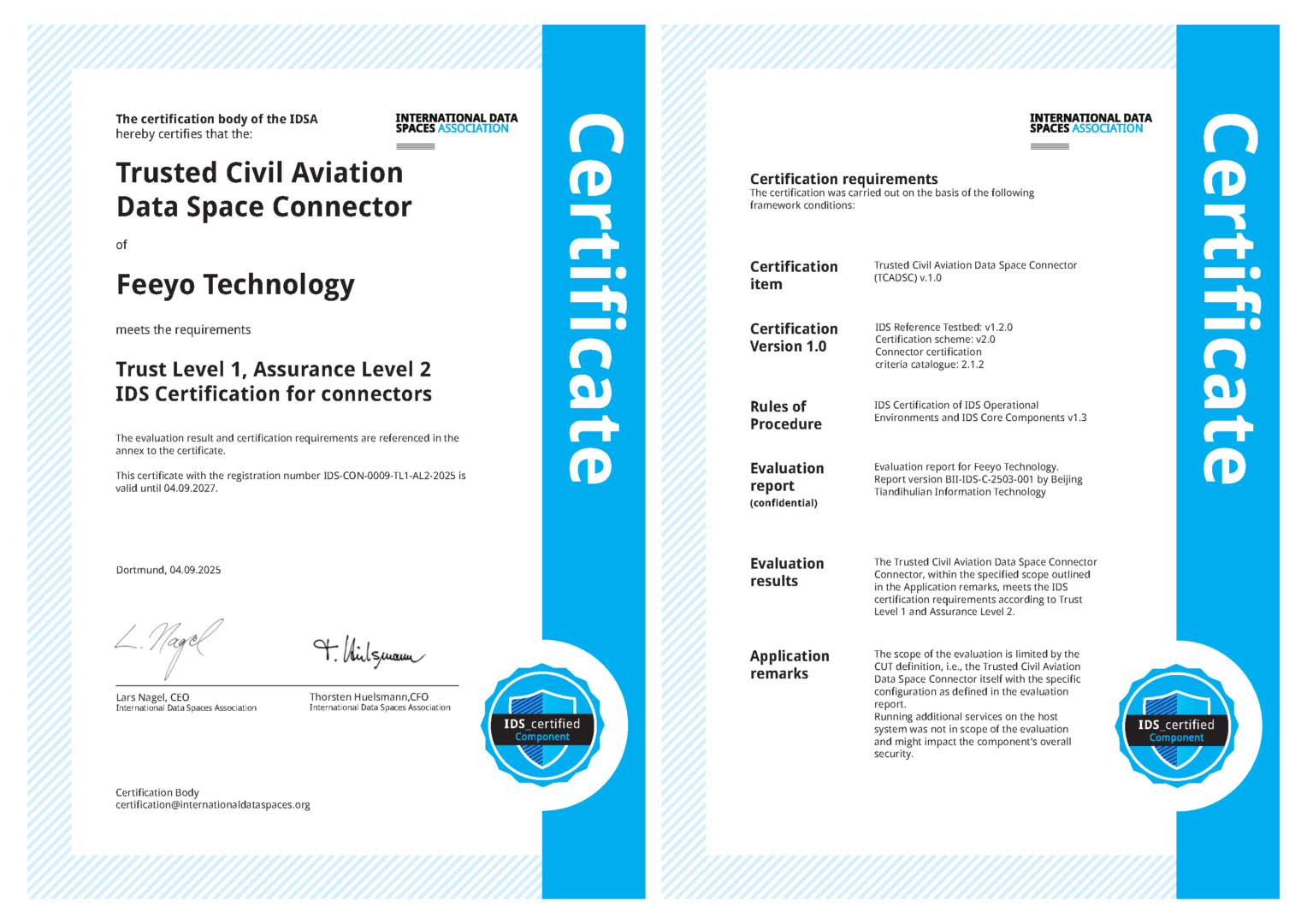
Feeyo Technology Trusted Civil Aviation Data Space Connector
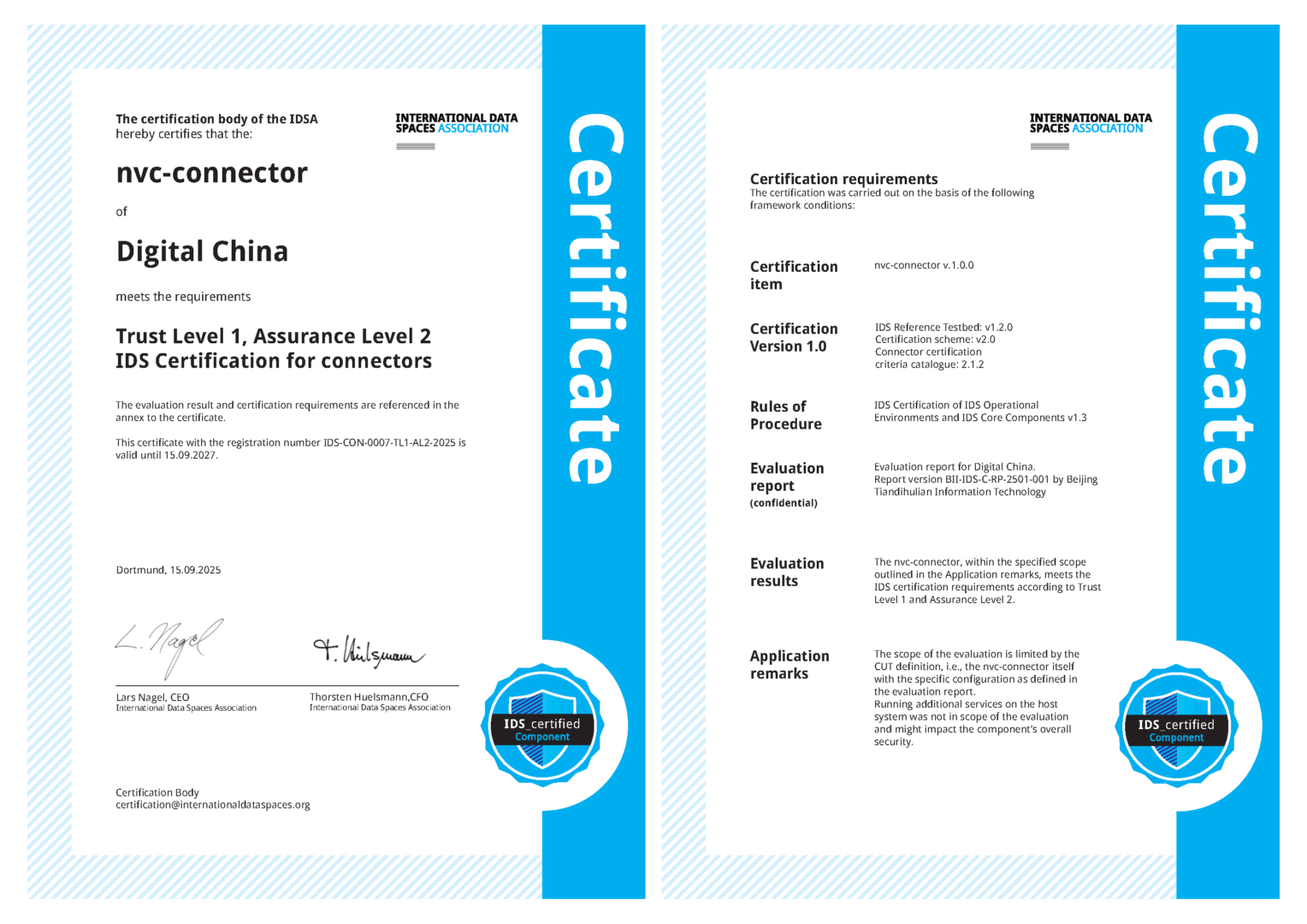
Digital China nvc-connector
China Mobile Communications Group Digital Mobile Trustworthy Data Space Connector

China Telecom Xinghai Data Space Connector

China Unicom Global Trusted Data Space Connector