
IDSA Data Space Connector Report
Table of Contents
- Editorial
- 1. Introduction
- 1.1 The Data Space Connector Report
- 1.2 Why Do We Need Data Space Connectors?
- 1.3 What is a Data Space Connector?
- 1.4 Interoperability of Data Space Connectors
- 1.5 Purpose and use of this report
- 2. Data Space Connectors
- 2.1 Amadeus EDC Connector
- 2.2 Eclipse Dataspace Components
- 2.3 Eclipse Tractus-X EDC Connector
- 2.4 Tekniker Dataspace Connector
- 2.5 TNO Security Gateway (TSG)
- 3. Conclusion
- Appendix A: Connectors partially compatible with the Dataspace Protocol
- DSP TRUE Connector
- Prometheus-X Dataspace Connector
- Appendix B: Certified connectors
- Appendix C: Overview of connectors from previous reports
Editorial
Dear Reader,
Welcome to the Data Space Connector Report.
We are excited to introduce the Data Space Connector Report, marking the beginning of a new era in data spaces. Building on the insights and achievements of the past two years from the Data Connector Report, this new publication will be your go-to resource for the latest information on Data Space Connectors that support the Dataspace Protocol (DSP). As the DSP moves towards becoming an international standard, it promises to revolutionize data sharing by ensuring interoperability and bridging diverse systems.
The Dataspace Protocol Technology Compatibility Kit (DSP TCK) is the official test suite that verifies whether a connector correctly implements the DSP, serving as a benchmark for interoperability. Our focus will be on connectors that have successfully passed the TCK testing, providing you with reliable information to make informed decisions. Published regularly by the International Data Spaces Association (IDSA), this report will be essential for anyone interested in the evolving landscape of data spaces technology.
We look forward to exploring this exciting journey with you and thank all our contributors and supporters for their continued dedication.
1. Introduction
1.1 The Data Space Connector Report
The Data Space Connector Report is a key regular publication from IDSA offering a comprehensive overview of Data Space Connectors and their role in interoperable data spaces.
In particular, the Data Space Connector Report:
- highlights the importance of Data Space Connectors, explaining what they are and why they are a key element in data spaces.
- It provides a summary of all the key requirements to make Data Space Connectors interoperable (e.g. relying on standards, having clear specifications, enabling semantic interoperability via the Data Catalog Vocabulary (DCAT) and specific vocabularies, etc.) based on the Dataspace Protocol.
- It gives visibility to existing connector implementations, provides details about them and follows their evolution over time.
- It is the reference point for learning and fostering interoperability in data sharing ecosystems.
Please note that the Data Space Connector Report aims to focus on the above-listed topics, therefore details on IDS use cases are not in scope. For a deep dive into those topics, please refer to some complementary IDSA resources:
Regarding the topic of use cases: Please refer to the Data Spaces Radar. It is an interactive tool created by IDSA in the context of the Data Spaces Support Center (DSSC) to offer an overview and quick information on several data spaces initiatives and use cases, highlighting their different implementation stages, domains and providing several additional details. The information is constantly updated by IDSA within the Data Spaces Support Centre project.
If you are maintaining a data space connector and would like it to be listed in this report, please submit your information via our submission form. For any questions, feel free to contact us.
1.2 Why Do We Need Data Space Connectors?
Participants in a data space need Data Space Connectors to share data – because connectors enable secure and effective communication and exchange in data spaces. They are a tool to connect many data endpoints to increase the pool of available data and to accelerate the data economy. By linking Data Space Connectors, data spaces become protected environments where participants can freely share data. Data sovereignty, transparency and fairness are ensured by adherence to a set of rules. Data Space Connectors act as nodes in a data space and provide the required level of data sovereignty to the participants.
Sharing and exchanging data is not a new thing, but the requirements for it are evolving. A Data Space Connector essentially realizes two relevant aspects: It provides data exchange services that are (1) the Application Programming Interface (API) to other participants in a data space to achieve interoperability and (2) the trustworthy component to handle data by implementing policy enforcement mechanisms and a common baseline for cybersecurity. However, as data can be different and the requirements for data sharing can be different as well, variants of connectors are needed (see the IDS RAM section 2.2 and section 2.4 for more information). This report provides an overview of these data connectors, their purpose, use and distinctions, but all based on the same foundational specification to provide system interoperability in data spaces, the Dataspace Protocol.
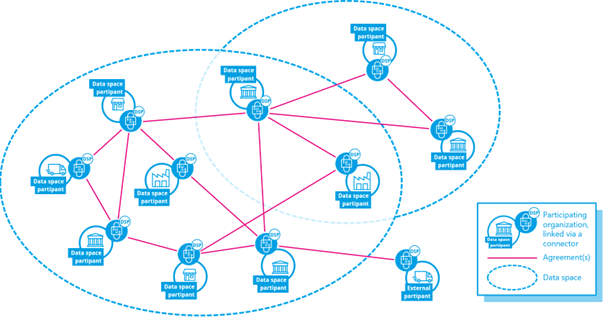
Figure 1 Data Space Connectors supporting the Dataspace Protocol enable scalability and interoperability, thus allowing true n-to-m data sharing.
Figure 1 shows how Data Space Connectors, built on the Dataspace Protocol, form the backbone of scalable and interoperable data exchange within and across domains. They enable connections between multiple participants and technical environments, ensuring secure, and trustworthy data sharing. While the deployment model may vary depending on the digital capabilities of the organization or other requirements, the Data Space Connector will enable interoperability and put data to use, to link it with other data and to support modern concepts such as (shared and distributed) digital twins, AI, or federated learning. To do so, the Data Space Connectors realize archetypical patterns for deployment models, e.g., orchestrate cloud-based service, lightweight API gateways, or IoT gateways.
While the requirements for data sovereignty, i.e., the ability to express and enforce the rights and obligations, the usage policies, are different in such scenarios, a need for basic interoperability of usage policies is fundamental for Data Space Connectors to build interoperable data spaces.
1.3 What is a Data Space Connector?
Data Space Connectors are essential for enabling trust and interoperability in data sharing and exchange within data spaces, which are designed to provide data sovereignty. Data spaces, and with that, data sovereignty will be the level playing field on a global scale. This represents a significant advantage and revolutionizes the data economy of the future – with the goal of benefiting society, businesses, and individuals.
New data spaces may have different implementations and standards, which can lead to the creation of new data silos. Therefore, a strong push for convergence is needed to enable interoperability, data continuity, and common governance models that support data sovereignty for all data spaces. The IDSA Rulebook provides an overview of the functional requirements of a data space, the fundamental structure, and introduces the mandatory and optional functionalities of a data space.
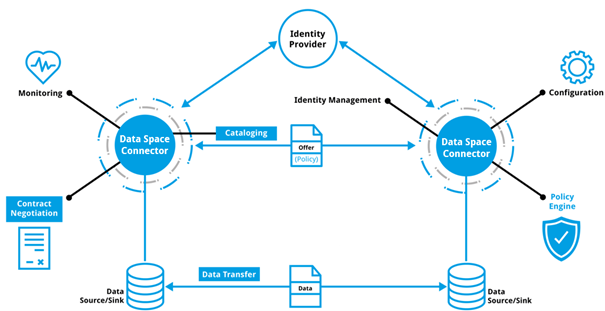
Figure 2 Data exchange services realized by a data connector as described in the IDS-RAM section 3.5.2
IDSA’s core role is developing and maintaining a reference architecture for data sharing and exchange that prioritizes data sovereignty in data-driven business ecosystems. The IDSA has created a global standard and Reference Architecture Model (RAM) that facilitates secure and self-determined data sharing between trusted parties across various ecosystems.
Certified users gain access to the data ecosystem and attach usage restriction policies to their data before making it available to other users. The Data Space Connector is a central component of the IDS standard and enables data exchange services as described in the IDS-RAM section 3.5.2.
The IDS Certification was launched in 2022 to prove compliance with the IDS requirements defined by the IDSA Certification Working Group. It offers different trust and assurance levels for both connectors and operational environments. Before its launch, a pre-certification for connectors, known as ‘IDS-Ready’, was available to support companies in preparing for certification via a third-party assessment.
The IDS standard addresses technical, operational, and legal agreements in data spaces, which combine technical, organizational, and legal complexities. It provides guidelines for data sharing and adds features such as identity management, communication security, and usage control. The Data Space Connector builds on various international standards from ISO/IEC, CEN/CENELEC, IEEE, and W3C.
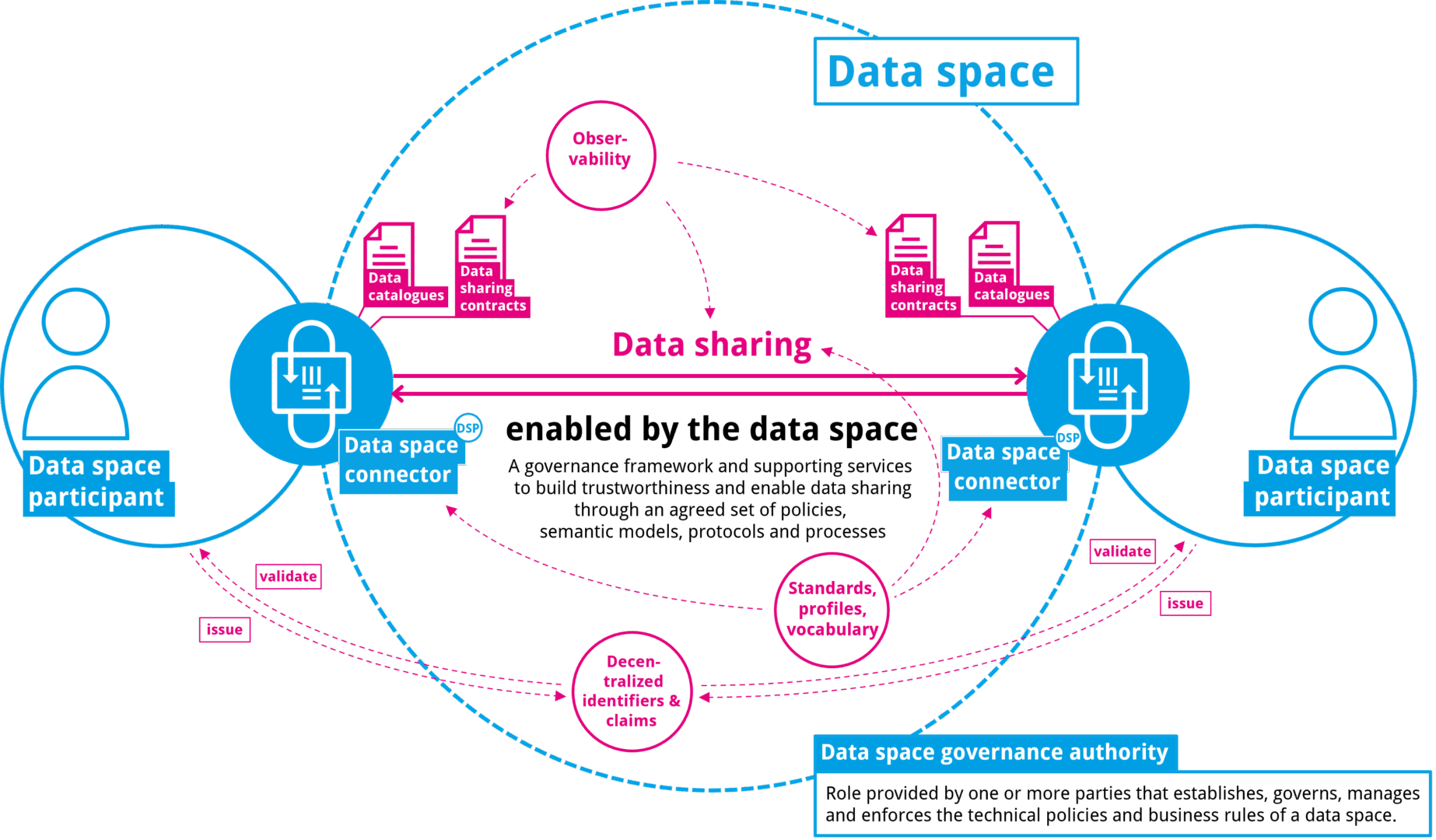
Figure 3 Fundamental concepts of a data space, their roles and interactions. At its core: the Dataspace Protocol supporting the Data Space Connectors to ensure interoperability and bridge diverse systems.
The foundation for Data Space Connectors is the Dataspace Protocol, providing an interoperability specification for the control plane of Data Space Connectors. The Dataspace Protocol 2025-1 was published as a final release 1.0.0 in July 2025. This version will be included in the IDS Certification. The Dataspace Protocol TCK is the official test suite used to verify whether a Data Space Connector correctly implements the Dataspace Protocol. An implementation successfully passing the Dataspace Protocol TCK is interoperable with other compliant implementations. The DSP TCK thus serves as a benchmark for interoperability and a learning tool for both developers and organizations evaluating Data Space Connectors. While many Data Space Connectors exist, those tested against the DSP TCK provide an objective measure of compliance with the Dataspace Protocol, helping users understand interoperability expectations while acknowledging that other connectors may also be viable.
This Data Space Connector Report focuses on the implementation of the Dataspace Protocol and provides further distinguishing information about the Data Space Connector variants to provide guidance on identifying relevant projects supporting data space participants in connecting to others by the means of a data space (for the fundamental concepts of a data space, their roles and interactions, see figure 3).
1.4 Interoperability of Data Space Connectors
Data is one of the most valuable assets in the digital economy, but its potential value can only be realized if it can move and interact with other data to produce insights that create value. For this, it must be possible for data to be shared and reused in a trusted way. Interoperability is the ability of different systems and organizations to exchange, understanding, and use of data, is essential for enabling data sharing and creating value in data ecosystems. Data spaces help to establish a common understanding of trust, and provide a mechanism to establish sharing contracts, which include access and usage policies that ensure the protection and accountability of data providers and data consumers. As data spaces become more prevalent and diverse, there is also a growing need for intra- and cross-data spaces interoperability.
Different data spaces may have different goals, architectures, business models, and governance structures, depending on the authority or community that drives them. To avoid fragmentation and duplication of efforts, participants in these data spaces need to communicate in an interoperable way with each other and across multiple data spaces, following common standards and principles.
Interoperability can be achieved at different levels, depending on the degree of integration and alignment of the data and systems involved. Two well-known frameworks that define interoperability levels are the ISO/IEC 19941 standard for cloud computing interoperability and portability, and the European Interoperability Framework for public services. Both frameworks identify four main levels of interoperability: technical (transport & syntactic), semantic, organizational, and legal:
- Technical interoperability refers to the physical and logical connections between systems and data sources, such as protocols, interfaces, and formats. This includes syntactic interoperability which refers to the structure and syntax of the data exchanged, such as schemas, models, and vocabularies.
- Semantic interoperability refers to the meaning and interpretation of the data, such as concepts, relationships, and ontologies.
- Organizational interoperability refers to the processes, policies, and governance of data sharing, such as roles, responsibilities, and agreements.
- Legal interoperability refers to the acceptance of legal equivalence of contracts and contractual clauses between different data ecosystems. These ecosystems can have differences on multiple dimensions, based for example on industry regulations, or national laws but also contractual statements with identical wordings might have diverging interpretations in different data ecosystems.
More information on data space interoperability is provided in the IDSA Rulebook. This Data Space Connector Report focuses on the technical interoperability aspects realized by the Dataspace Protocol.
1.5 Purpose and use of this report
This report provides a concise overview of data space connectors that have been tested with the Dataspace Protocol Technology Compatibility Kit. The DSP TCK is the official toolset used to verify whether a connector correctly implements the Dataspace Protocol. The goal is not to recommend a “best” connector, but to document each implementation’s compliance with the Dataspace Protocol in a transparent and comparable way.
Each connector entry includes:
- General information: name, maintainer, website, short description, license
- Technical compliance details: Dataspace Protocol version, TCK version, test output, and configuration used
The report is intended as a reference. It is updated regularly to reflect new data space connectors, new protocol versions, and updated compliance results.
2. Data Space Connectors
This chapter presents the connectors tested with the Dataspace Protocol TCK. For each connector, the following information is provided:
- Name – Connector name
- Maintainer – Organization responsible for the connector
- Website – Official connector or organization website
- Description – Short overview of the connector, describing Unique Selling Point and/or main field of application of the connector (e.g., cloud, IoT)
- License – type (open source / proprietary) and/or details where applicable
- Dataspace Protocol Version – DSP version supported
- TCK Version – Version of the TCK used in testing
- Test Output – Result of the compliance tests (full or partial)
- Configuration Used – Main setup parameters relevant for the test
Amadeus EDC Connector

Technical Compliance Details
Eclipse Dataspace Components
Technical Compliance Details
Eclipse Tractus-X EDC Connector

Technical Compliance Details
Tekniker Dataspace Connector

Technical Compliance Details
TNO Security Gateway (TSG)
Technical Compliance Details
3. Conclusion
This report highlights the central role of data space connectors in enabling interoperability within data spaces. By documenting their technical compliance, features, and adoption scenarios, it provides a snapshot of the current state of play and a basis for comparison across implementations.
The Data Space Connector Report is intended as a living document. New insights, feedback, and updated information are essential to keeping it relevant and comprehensive. Readers are invited to contribute by sharing corrections, additions, or further connector details through the submission form or by contacting the IDSA team.
In this edition, the Data Space Connector Report focuses exclusively on data space connectors that have undergone testing against the Dataspace Protocol Technical Competability Kit (TCK). This ensures a consistent and comparable view of technical compliance.
Connectors partially compatible with the Dataspace Protocol and IDS-certified connectors are included in the appendices to provide additional context and reference. Historical connector data from previous editions is also included to maintain continuity. For a broader overview of connectors, see previous editions of the report.
Annexes
Appendix A: Connectors partially compatible with the Dataspace Protocol
This appendix lists connectors that have only partially passed TCK testing. It provides context for readers while keeping the main connector chapter focused on fully compliant implementations.
DSP TRUE Connector

Technical Compliance Details
Prometheus-X Dataspace Connector

Technical Compliance Details
Appendix B: Certified connectors
This appendix lists connectors that have been certified under the IDS scheme.
| Connector name | Date | Assurance level |
|---|---|---|
| Telekom DIH Connector by T-Systems | Dec 2023 | Level 2 – Concept Review |
| VTT DSIL Connector | Feb 2024 | Level 2 – Concept Review |
| TNO Security Gateway | Mar 2024 | Level 2 – Concept Review |
| TRUE Connector by Engineering | Apr 2024 | Level 2 – Concept Review |
| GATE Dataspace Connector | Aug 2024 | Level 1 – Checklist approach |
| Exchange Data Space (EDS) Connector by Huawei | Oct 2024 | Level 2 – Concept Review |
| Trusted Civil Aviation Data Space Connector by Feeyo Technology | Sep 2025 | Level 2 – Concept Review |
| nvc-connector by Digital China | Sep 2025 | Level 2 – Concept Review |
| China Mobile Communications Group Digital Mobile Trustworthy Data Space Connector | Sep 2025 | Level 2 – Concept Review |
Appendix C: Overview of connectors from previous reports
Figure 4 contains a condensed version of the connector overview from previous editions of the report. It is included for reference purposes and will not be updated in future editions.
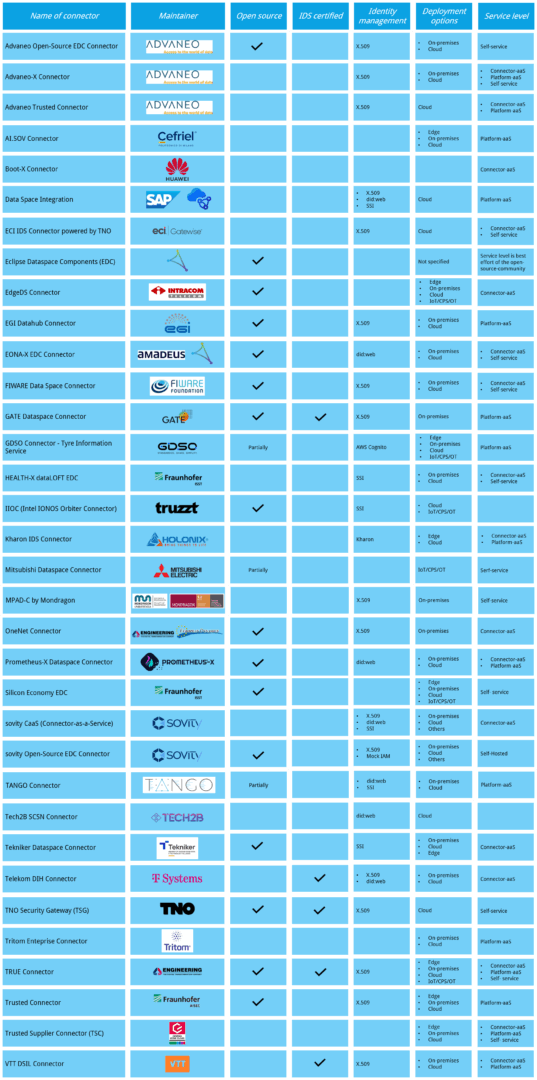
Figure 4 Overview of connectors from previous editions of the Data Connector Report.







